Differential Power Analysis IP
Filter
Compare
38
IP
from
9
vendors
(1
-
10)
-
10G PHY for Differential Buffer, TSMC N6, North/South (vertical) poly orientation
- Compliant with the PCI Express (PCIe®) 3.1, 2.1, 1.1 and PIPE specifications
- x1, x2, x4, x8, x16 lane configurations with bifurcation
- Multi-tap adaptive and programmable Continuous Time Linear Equalizer (CTLE) and Decision Feedback Equalization (DFE)
- L1 substate and SRIS support
-
10G PHY for Differential Buffer, TSMC N3E, North/South (vertical) poly orientation
- Compliant with the PCI Express (PCIe®) 3.1, 2.1, 1.1 and PIPE specifications
- x1, x2, x4, x8, x16 lane configurations with bifurcation
- Multi-tap adaptive and programmable Continuous Time Linear Equalizer (CTLE) and Decision Feedback Equalization (DFE)
- L1 substate and SRIS support
-
10G PHY for Differential Buffer, GF 12LP, North/South (vertical) poly orientation
- Compliant with the PCI Express (PCIe®) 3.1, 2.1, 1.1 and PIPE specifications
- x1, x2, x4, x8, x16 lane configurations with bifurcation
- Multi-tap adaptive and programmable Continuous Time Linear Equalizer (CTLE) and Decision Feedback Equalization (DFE)
- L1 substate and SRIS support
-
10G PHY for Differential Buffer, TSMC N7, North/South (vertical) poly orientation
- Compliant with the PCI Express (PCIe®) 3.1, 2.1, 1.1 and PIPE specifications
- x1, x2, x4, x8, x16 lane configurations with bifurcation
- Multi-tap adaptive and programmable Continuous Time Linear Equalizer (CTLE) and Decision Feedback Equalization (DFE)
- L1 substate and SRIS support
-
Differential Buffer, TSMC N5, North/South (vertical) poly orientation
- Compliant with the PCI Express (PCIe®) 3.1, 2.1, 1.1 and PIPE specifications
- x1, x2, x4, x8, x16 lane configurations with bifurcation
- Multi-tap adaptive and programmable Continuous Time Linear Equalizer (CTLE) and Decision Feedback Equalization (DFE)
- L1 substate and SRIS support
-
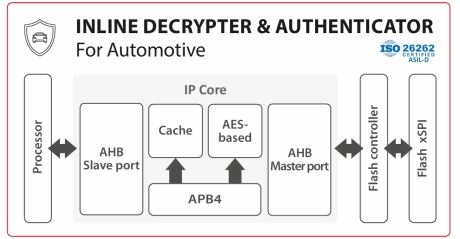
Inline Decrypter & Authenticator IP Core for Automotive
- The Inline Decrypter and Authenticator IP core enables on-the-fly execution of encrypted and signed code from Flash.
- It is used to authenticate and decrypt code located in Flash. In addition it is ISO26262 certified (ASIL-D).
-
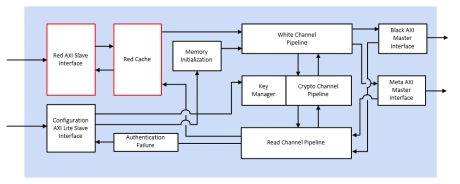
Inline memory encryption engine, for FPGA
- Performs encryption, decryption and/or authentication using AES Counter Mode (CTR) or Galois Counter Mode (GCM)
- Supports AES key sizes 128 or 256
- Internal key management with NIST-compliant key generation
- Encrypt memory space into user-defined vaults, each with a unique key
- Compatible with AMBA AXI4 interface
- Supports hard or soft memory controllers in Xilinx FPGA and SoC devices
- Supports multiprocessor systems
-
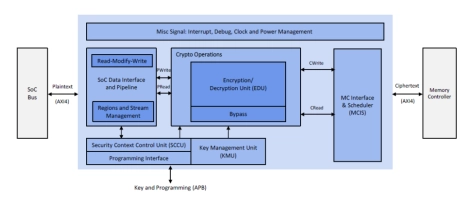
Inline memory encryption engine for ASIC SoCs
- 128/512-bit (16-byte) encryption and decryption per clock cycle throughput
- Bidirectional design including separate crypto channels for read and write requests, ensuring non-blocking Read
- Read-modify-write supporting narrow burst access.
- Zeroization and support for memory initialization
- Latency: <28 clock cycles for unloaded READ
-
Programmable Root of Trust With DPA and FIA for US Defense
- Custom-designed 32-bit secure RISC-V processor
- Multi-layered security model protects all core components against a wide range of attacks
- Security model includes hierarchical privilege model, secure key management policy, hardware-enforced isolation/access control/protection, error management policy
- State-of-the-art DPA resistance, FIA protection and anti-tamper techniques
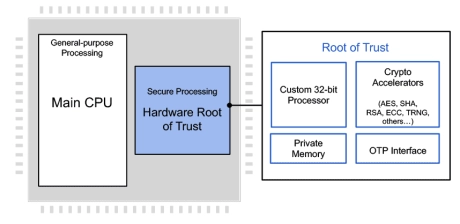
-
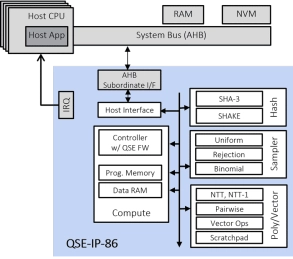
Fast Quantum Safe Engine for ML-KEM (CRYSTALS-Kyber) and ML-DSA (CRYSTALS-Dilithium)
- The Quantum Safe Engine (QSE) IP provides Quantum Safe Cryptography acceleration for ASIC, SoC and FPGA devices.
- The QSE-IP-86 core is typically integrated in a hardware Root of Trust or embedded secure element in chip designs together with a PKE-IP-85 core that accelerates classic public key cryptography and a TRNG-IP-76 core that generates true random numbers.