DPA Resistant IP
Filter
Compare
6
IP
from
4
vendors
(1
-
6)
-
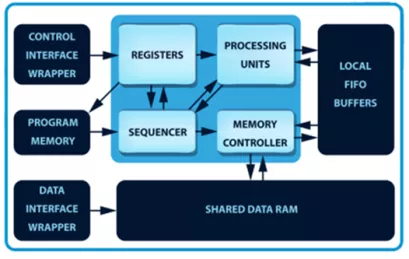
ChaCha20 DPA Resistant Crypto Accelerator
- Quicken time-to-market using precertified DPA Countermeasures
- Highly secure cryptographic engine primitives
- Extensive validation using the Test Vector Leakage Assessment (TVLA) methodology (revealing no leakage beyond 100 million traces)
- Cores protected against univariate first- and second-order side-channel attacks beyond 1 billion operations
-
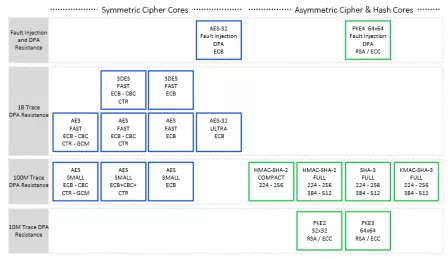
DPA Resistant Software Library
- Library implements a very high-security primitives for AES, ECC, RSA, and SHA
- Supported platforms: ARM Cortex-A9, ARM7TDMI, and others
- AES supports 128/192/256-bit encrypt and decrypt
- ECC supports ECDSA/ECDH for NIST prime fields (192/256/384/521)
-
Attack resistant ECC hardware acceleration core
- Supports any EC over GF(p) of the simplified Weierstrass form that is commonly defined in ECC standards such as NIST, SEC2, Brainpool
-
Root of Trust - Foundational security for SoCs, secure MCU devices and sensors
- Secure Boot assist to host CPU(s) and protection of key material
- Secure firmware upgrade management for Host CPU
- Lifecycle management support
- Secure Debug support
-
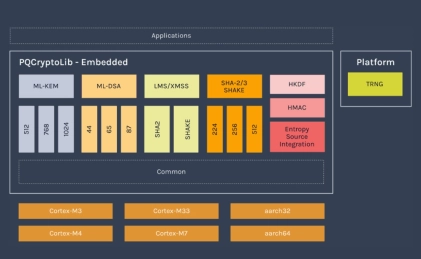
Highly-optimized PQC implementations, capable of running PQC in under 15kb RAM
- PQCryptoLib-Emebedded is a versatile, CAVP-ready cryptography library designed and optimized for embedded devices.
- With its design focused on ultra-small memory footprint, PQCryptoLib-Embedded solutions have been specically designed for embedded systems, microcontrollers and memory-constrained devices. It provides a PQC integration to devices already in the field.
-
Centralised Real Time Processor IP Core
- CryptOne programmed algorithms:
- Constant time modular exponentiation
- Constant time, parallel modular exponentiation CRT
- Constant time ECDSA sign/verify