Public Key Accelerator IP
Welcome to the ultimate Public Key Accelerator IP hub! Explore our vast directory of Public Key Accelerator IP
All offers in
Public Key Accelerator IP
Filter
Compare
43
Public Key Accelerator IP
from 18 vendors
(1
-
10)
-
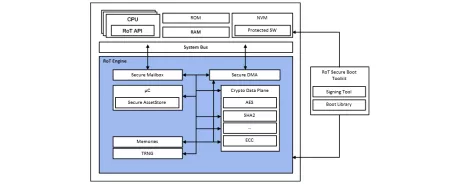
Root of Trust - Foundational security in SoCs and FPGAs for IoT clients and sensors
- Secure Boot assist to host CPU(s) and protection of key material
- Secure firmware upgrade management for Host CPU
- Lifecycle management support
- Secure Debug support
- Secure device authentication and identity protection
-
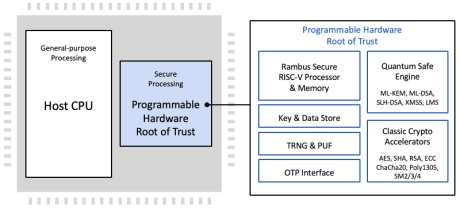
Programmable Root of Trust with Quantum Safe Cryptography acceleration
- The CryptoManager RT-6xx family protects against a wide range of hardware and software attacks through state-of-the-art side channel attack countermeasures and anti-tamper and security techniques.
- The RT-6xx supports various security certifications up to level 3. The RT-6×4 Root of Trust adds Quantum Safe Encryption (QSE) to provide a future-proof hardware security solution to protect data center assets starting today and into the quantum era.
-
Asymmetric Public Key Cryptography IP
- Constant time of the basic arithmetic unit: protection against timing attacks.
- Regular modular exponentiation (RSA): protection against SPA.
- Regular ECSM: protection against SPA.
- Protection against CPA and collision attacks.
- Protection against Address-bit CPA.
- Protection against fault attacks.
-
Public Key Crypto Engine
- ASIC & FPGA
- RSA, ECC and more
- 100% CPU offload
- DPA countermeasures
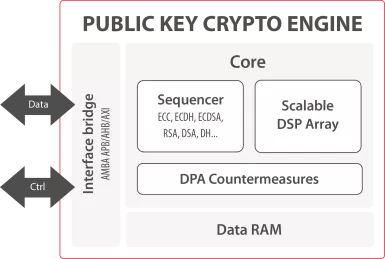
-
RSA-ECC High-Performance Multi Public Key Engine
- RSA, ECC and more
- > 1 GHz in 16nm
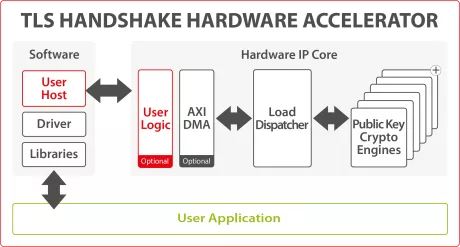
-
Public Key Accelerator
- Modular exponentiation operations with up to 4096-bit modulus
- Prime field ECC operations with up to 571-bit modulus
- Fastest implementation is 58 kGE and 68 Op/s for 2048-bit RSA, 431 Op/s for 1024-bit RSA, 150 Op/s for 384-bit scalar multiplication
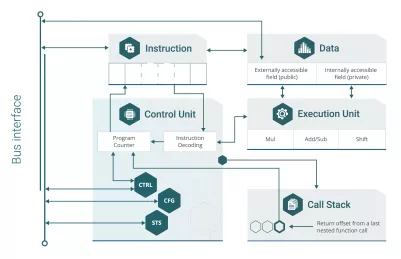
-
100% Secure Cryptographic System for RSA, Diffie-Hellman and ECC with AMBA AHB, AXI4 and APB
- For RSA, Diffie-Hellman and ECC
- With AMBA AHB, AXI4 and APB
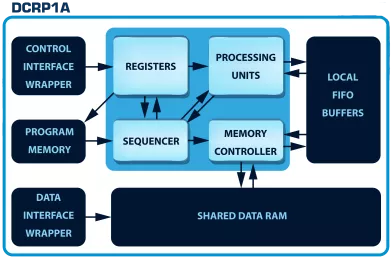
-
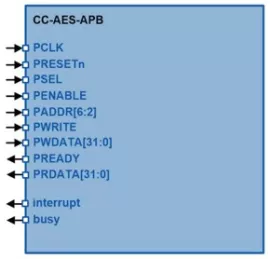
Advanced Encryption Standard Module
- AMBA APB3 bus
- Encryption and decryption
- ECB mode
- Programmable key length
-
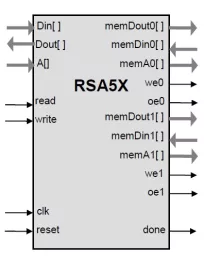
Scalable RSA and Elliptic Curve Accelerator
- Small size: RSA5X starts from less than 15K ASIC gates
- Implements the computationally demanding parts of RSA public key cryptography for long life battery powered applications
-
RSA Public Key Exponentiation Accelerator
- Small size: RSA1-E starts from less than 10K ASIC gates (intermediate result storage memory required; size depends on the core configuration)
- Implements the computationally demanding parts of RSA public key cryptography for long life battery powered applications
- Support for RSA binary fields of configurable bit sizes up to 2048
- Microprocessor-friendly interface