This is a Security and Safety compliance block.
SOC designers/ SW Architects can distinguish memory ranges which may carry sensitive information, which can be leaked out by SPA/DPA.
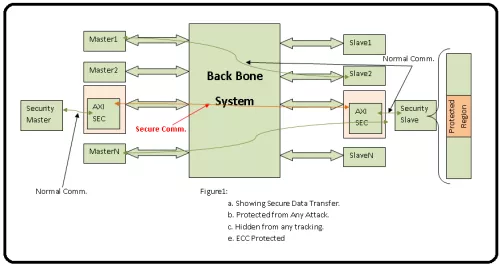
This block will hide the communication on range of programmed addresses.
Also, it has ECC which is SEC-DED, which will ensure that the transaction is secure while travelling on the backbone system.
One cannot manipulate the secured range of addresses and cannot change data on those addresses.
Security Gasket to hide transaction to range of addresses for SPA and DPA and secure Data using End-to-End ECC.
Overview
Key Features
- 1. AMBA-AXI-4.0 Master and Slave
- 2. Blocks user to snoop the meaningful data.
- 3. Block User from SPA/ DPA Gassing the secure data.
- 4. End to End ECC Secured transactions.
- 5. ECC is SEC-DED.
Benefits
- 1. Specified Memory content is protected and secured.
- 2. Blocks DPA and SPA of Data.
- 3. Debug ports can snoop Bus Data but cannot make any meaning out.
- 4. Both Master and Slave components are available.
- 5. Full Support of standard AMBA-AXI-4.0.
- 6. Throughput and Performance is 100%.
Block Diagram
Applications
- 1. On Interface of Security MASTER which communicate to System and want to read sensitive data from specified secure address.
- 2. On Security Slave which carry Secure memory region which carry the sensitive information.
Deliverables
- 1. Synthesizable RTL Code.
- 2. Testbench.
- 3. Usage Guide.
Technical Specifications
Maturity
Final, Stable, Tested
Availability
Available
Related IPs
- Security Gasket to hide transaction to range of addresses for SPA and DPA and secure Data using End-to-End ECC.
- AES - Encrypts sensitive data to ensure secure communication and transactions
- Programmable Root of Trust With DPA and FIA for US Defense
- Flash Memory Controller IP, Support page sizes of 512, 2K, 4K, 8K and 16K bytes NAND Flash memory, 74bit ECC correction (512 or 1K bytes sectors), Soft IP
- Fast Quantum Safe Engine for ML-KEM (CRYSTALS-Kyber) and ML-DSA (CRYSTALS-Dilithium) with DPA
- Inline cipher engine for PCIe, CXL, NVMe, 5G FlexE link integrity and data encryption (IDE) using AES GCM mode