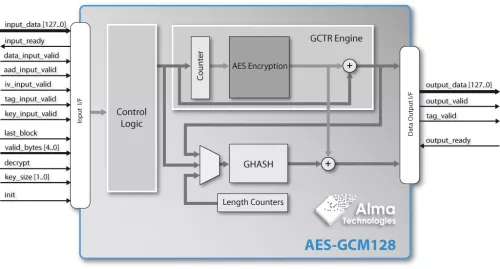
The AES-GCM128 core from Alma Technologies implements the GCM-AES authenticated encryption and decryption, as specified in the NIST SP800-38D recommendation for GCM and GMAC and the FIPS-197 Advanced Encryption Standard. The core can be programmed to encrypt or decrypt 128-bit blocks of data, using 128-, 192-, or 256-bit cipher-key. In addition, using the GHASH algorithm a Hash value - the TAG - is calculated for the encrypted, or the additional plaintext, data. Then, in decryption mode, the calculated TAG is compared with the TAG that accompanies the ciphertext data and a Fail or Pass flag is accordingly generated.
The AES-GCM128 core uses 128-bit datapath, needing 1 clock cycle to load or unload each 128-bit plaintext or ciphertext data block. A Key Expander module is included in the AES-GCM128 and automatically generates the AES Round Key Values. All internal operations are performed on 128-bit words and, for each HASH, only 12/14/16 clock cycles are required per 128-bit block for 128/192/256-bit cipher-key size respectively. The AES-GCM128 core supports 96-bit Initialization Vectors and input/output TAGs of configurable length.
The AES-GCM128 core is equipped with easy-to-use fully stallable interfaces for both input and output. These are designed to permit the user application to pause the produced output data stream when it is not able to receive data, or to pause the input stream towards the core according to data arrival rate.
GCM-AES Authenticated Encryption & Decryption
Overview
Key Features
- Compliant, High-Performance and Standalone Operation
- Advanced Encryption Standard (AES - FIPS PUB 197) and NIST SP800-38D for GCM/GMAC compliance
- Run-time programmable encryption or decryption operation
- Run-time programmable cipher-key size: 128-, 192-, 256-bit
- Integrated Key Expansion module for automatic generation of the AES Round Key values
- 96-bit GCM Initialization Vector
- GMAC operation supported: Additional Authenticated Data input, without encryption
- Comparison between the input TAG and the generated TAG during decryption
- 12/14/16 clock cycles per 128-bit block for 128/192/256-bit cipher-key size respectively
- 12 clock cycles per HASH operation
- High-speed, flow controllable, streaming I/O data interfaces
- Trouble-Free Technology Map and Implementation
- Fully portable, self-contained RTL source code
- Strictly positive edge triggered design
- D-type only Flip-Flops
- Fully synchronous operation
- No special timing constraints required
- No false paths
- No multi-cycle paths
Block Diagram
Deliverables
- Clear text VHDL or Verilog RTL source for ASIC designs, or pre-synthesized & verified Netlist for Altera, Lattice, Microsemi and Xilinx FPGA and SoC devices
- Release Notes, Design Specification and Integration Manual documents
- Bit Accurate Model (BAM) and test vector generation binaries, including sample scripts
- Self checking testbench environment, including sample BAM generated test cases
- Simulation and sample Synthesis (for ASICs) or Place & Route (for FPGAs) scripts
Technical Specifications
Availability
NOW