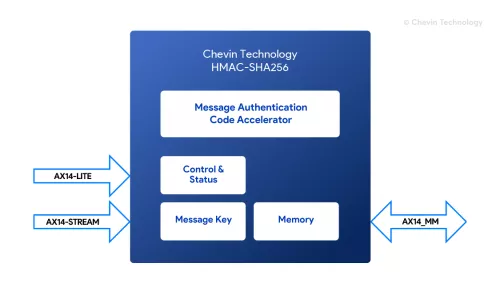
Chevin Technology’s HMAC-SHA256 cryptographic accelerator function is used to securely generate and verify message authentication codes. Message authentication is increasingly required by corporations, government organisations, and individuals to secure communications between sender and receiver. The HMAC – SHA256 authentication function is especially suited for cybersecurity, defense, and aerospace applications, and can be added to existing products, or designed into prototypes. Contact us for more information, or to discuss source code and netlist licensing options for Intel and AMD FPGAs and ASICs.
The all-RTL solution provides a fast and secure way to calculate a SHA256 hash for any message of any length. When combined with a secret key, it can also construct a HMAC keyed-hash message authentication code, which can be used to protect messages that are sent, and verify those that are received. The HMAC-SHA256 accelerator accepts multiple independent streaming messages/channels and support any number of arbitrary length messages. Number of channels is limited only by the memory resources provided, embedded Block RAM or external DDR. Typical use cases include highly secure RTL solutions where a CPU is unable to meet the required throughput and security performance.
HMAC-SHA256 Accelerator
Overview
Key Features
- Hardware Root of Trust
- Widely used password hash algorithm
- Security Critical HTTP, SSL, TLS
- Key storage in Private memory
- Reduce Risk of cyber hacks, copying, cloning
- HMAC-SHA256 Message Authentication
- All-RTL security solution in Hardware
- Multi-channel operation with AXI4_STREAM
- Securely generate & verify keyed-hash MAC
- High Throughput >1M hashes /second @156MHz
- Seamless integration with AXI4_ST / AXI4_MM
- NIST FIPS 180-4 Secure Hash Standard
- RFC6234 SHA256 Secure Hash Algorithm
- NIST FIPS 198-1 HMAC Keyed-Hash MAC
Block Diagram