Rambus DPA Resistant HMAC-SHA-2 Cryptographic Accelerator Cores prevent against the leakage of secret cryptographic key material through attacks when integrated into an SoC or FPGA. HMAC-SHA-2 100 million trace DPA resistant cryptographic accelerator core.
The DPA Resistant Hardware cores offer chipmakers an easy-to-integrate technology-independent soft-macro security solution with built-in side-channel resistance for cryptographic functions across a wide array of devices.
These high-performance cores provide a higher level of protection than standard security cores, while improving time-to-market, as all the cores are validated DPA countermeasures. It is highly flexible for integration with standard cipher modes such as Cipher Block Chaining (CBC), Counter (CTR) and Authenticated Encryption mode / Galois Counter (GCM) modes. The fast AES core performs AES encryption with DPA protection using only 2 clock cycles per AES round, outperforming any existing solution.
HMAC-SHA-2 (224/256/384/512) 100 Million Trace DPA Resistant Crypto Accelerato
Overview
Key Features
- Quicken time-to-market using precertified DPA Countermeasures
- Highly secure cryptographic engine primitives
- Extensive validation using the Test Vector Leakage Assessment (TVLA) methodology (revealing no leakage beyond 100 million traces)
- Cores protected against univariate first- and second-order side-channel attacks beyond 1 billion operations
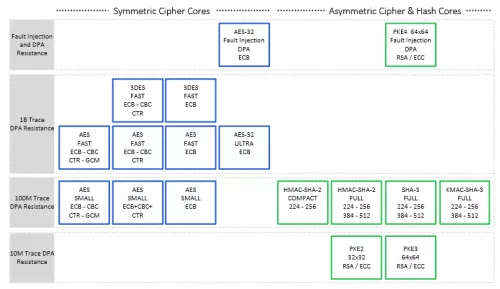
- DPARC cores are available for AES (128/256), 3DES, SHA-2 (224/256 or 224/256/384/512), HMAC-SHA-2 (224/256 or 224/256/384/512), RSA, ECDSA, and ECDH
- Implements silicon proven and validated DPA countermeasures such as LMDPL (LUT-Masked Dual-rail with Pre-charge Logic) gate-level masking
- Simple control/status interface
- No routing constraints required
- Delivers highest level of security with side-channel resistance prioritized
- Also available as non-protected standard versions.
Benefits
- Side channel attack resistant
- Technology and node independent
- Superior cryptographic protection
- Use with any ASIC or FPGA
Block Diagram
Applications
- Government, Automotive, Military, Edge, IoT, Machine Learning (ML), Artifical Intelligence (AI), Semiconductor, Processors, Cryptocurrency
Deliverables
- Configurable Cryptographic Core: Verilog RTL reference design
- Synthesis Inputs: SDC constraint file suitable for FPGA or ASIC synthesis
- Full Documentation: Specification documents and Integration guides
- Functional Testbench: NIST-compliant test vectors
Technical Specifications
Foundry, Node
Any
Maturity
Silicon proven
Availability
Now
Related IPs
- AES-ECB 1 Billion Trace DPA & Fault Injection Resistant Crypto Accelerator
- AES-ECB 1 Billion Trace DPA Resistant Crypto Accelerator
- AES-ECB-CBC-CFB-CTR 1 Billion Trace DPA Resistant Crypto Accelerator
- AES-ECB-CBC-CFB-CTR-GCM 1 Billion Trace DPA & Fault Injection Resistant Crypto Accelerator
- AES-ECB-CBC-CFB-CTR-GCM 1 Billion Trace DPA Resistant Crypto Accelerator
- ChaCha20 DPA Resistant Crypto Accelerator