The TESIC-410 IP is a Common Criteria (CC) EAL5+ PP0084/PP0117 certification ready Secure Enclave available as a hard-macro for plug-and-play SoC integration.
The TESIC-410 Secure Enclave IP provides the highest level of security for an SoC. Patented design techniques and countermeasures against side channel and perturbation attacks ensure the high levels security whilst keeping power consumption to a minimum.
Cryptographic hardware accelerators provide efficient support for standard cryptography and security operations increasing throughput while respecting power constraints and security requirements.
The BootROM and secondary boot loader firmware manage the certified life cycle and enforce and assure security from manufacturing to deployment.
The TESIC-410 is based on propriety IP free of 3rd party rights and royalties.
SECURE ENCLAVE IP
Overview
Key Features
- CRYPTOGRAPHIC ACCELERATOR HARDWARE
- Secure AES crypto-processor
- Key sizes: 128, 192, 256
- ECB, GCM
- Secure DES / Triple DES crypto-processor
- Key sizes 56, 112, 168 (ECB, CBC)
- Secure PKA public key crypto-processor
- Secure AES crypto-processor
- Operations up to 4096 bits
- SHA2 hardware-accelerator
- Secure SHA3 hardware-accelerator
- CRC 16-bit
- True Random Number Generator (TRNG)
- Pseudo Random Number Generator (PRNG)
- Security sensors
- Glitch detector
- Temperature sensor
- Active shield
- CERTIFIED CRYPTOGRAPHIC LIBRARY
- AES
- Key sizes: 128, 192, 256 (ECB, CBC, CTR, CMAC, CCM)
- DES* / Triple DES
- Key sizes: 56*, 168 (ECB & CBC)
- ECC
- Key sizes up to 521 (ECDH, ECDSA, ECIES)
- RSA
- Key sizes up to 4096
- (Key generation, signing and verification, encryption/decryption)
- HASH
- Sizes: 160 & 224, 256, 384, 512 bits
- SHA1, SHA2, SHA3
- MAC
- HMAC, KMAC
- RANDOM
- NRBG, DRBG, PRNG
- * Not part of the certification
- AES
- SHA2 hardware-accelerator
Benefits
- We provide a full set of security services. We guarantee that an SoC that integrates our TESIC-410 Secure Enclave will obtain CC EAL5+ certification. We can provide a comprehensive service to manage the certification process; from liaising with your chosen laboratory, through preparation of the necessary extensive documentation required, to handling the day-to-day project management. We also have a provisioning and key management service. We can interface with your chosen manufacturing site to initially provision your SoC and further manage keys and authenticated firmware from your chosen 3rd party OS providers, maintaining the chain of trust. This is handled from our MSSR CC EAL6 audited and certified site in France. With our many years of experience with security and certification we can advise on the security requirements of your SoC to obtaining the certification of your site to meet MSSR (Minimum Site Security Requirements).
Block Diagram
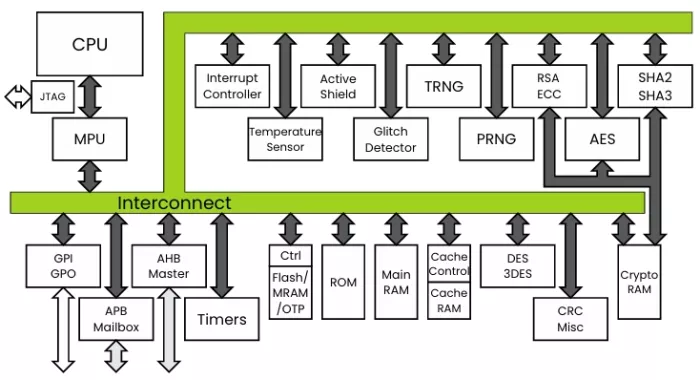
Applications
- Secured and Certified iSIM & iUICC
- EMVco Payment
- Hardware Crytocurrency Wallets
- FIDO2 Web Authentication
- V2X HSM Protocols
- Smart Car Access
- Secured Boot
- Secure OTA Firmware Updates
- Secure Debug
- ...and any design that requires a Secure Enclave, Secure Element or Hardware Root of Trust that is highly protected against side channel and perturbation fault attacks.
Deliverables
- TESIC-410 GDSII hard-macro, with .lib and .lef files (available for most modern processes, GF55, TSMC40, GF22 FDX, TSMC16...),
- Timing accurate functional model
- Verification environment
- Certified cryptographic software library and hardware drivers
- Full documentation
- Example code and quick start
- Complete support and guidance to achieve certification for all products that contain the TESIC-410 macro.
Technical Specifications
Foundry, Node
GF 55 LPx, TSMC 40 ULP, GF 22 FDX, TSMC 16 FFC
Maturity
Qualified and certified on various processes
Availability
Now