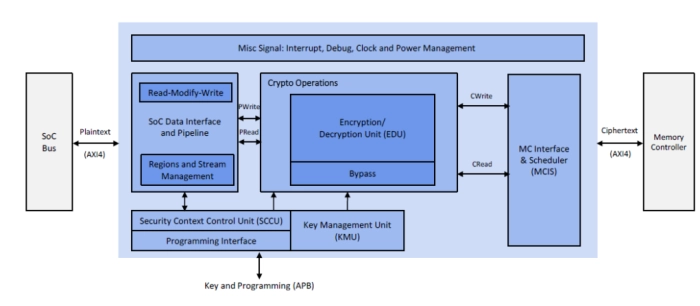
The IME-IP-341 is an SoC-ready, in-line memory encryption engine using AES/SM4 ciphers with XTS/ECB/Bypass as modes of operation. It incorporates multi-stream, multi-algorithm support required for supporting multiple virtual machines (e.g., Realms in ARMv9). It supports configurable protection of different memory regions (up to 32) with separate individual keys mapping to individual regions (e.g., PAS in MPE ARMv9).
The IME-IP-341 provides (optional) protection against power-analysis side-channel attacks by incorporating Differential Power Analysis (DPA) countermeasures within the cipher primitives. Additionally, Datapath Integrity (DI) using ECC based SRAMs with (optional) parity protection in the cipher datapath provides robustness against random errors, ensuring operation under stringent operating conditions in advanced technology nodes. For CMVP certification IME-IP-341 uses a CAVP certified cipher engine and (optional) built in known answer self-test (KAT).
How the IME-IP-341 Engine Works
The IME-IP-341 is an inline memory encryption engine for protection of off-chip memory. The programming for the security attributes and keys per region is programmed by a dedicated AMBA interface towards trusted subsystem. At the start, different memory regions (up to 32) can be programmed as per different security policies of the system.
Once the IP is programmed and initialized, it acts as a transparent datapath engine between the SoC bus and DDR controller. It also includes functionality to convert an encryption key into its equivalent decryption. Zeroization, and startup behavior is supported in compliance with MPE engine requirements for ARMv9. The IME-IP-341 supports programmable sector size (default is 64B, same as a typical cache line width and a typical DDR burst size).